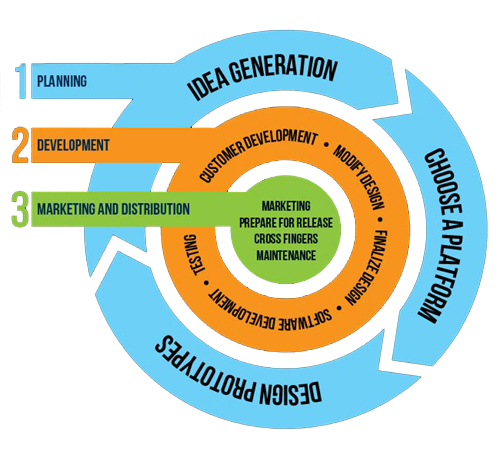
Phase 1: Planning
1. Idea Generation
Know your idea what you think of. We think on it, discuss its future use and its targeted audience.
2. Choose a platform
Think which platform will benifit the application most?
Windows, Android, IOS or Desktop Application?
3. Design Prototype
Next essential steps in the turning your idea into a design prototype which is simply defined and
have a three-dimensional version of your vision.
Phase 2: Development
1. Customer Development
Test the design with potential users to get feedback. It is far cheaper and faster to change things
around now than later
2. Modify Design
Decide what feedback is important and change your design accordingly. Keep doing customer
development untill we are satisfied.
3. Finalize Design
Pixel Perfection! Now Isn't that pretty?
4. Software Development
Get used to starting at the selected platform, clean and optimized code will win the race.
5. Testing
Internal testing is important, we make sure using a testing tool to help us to squesh little nesty
bugs.
Phase 3: Marketing and Distribution
1. Marketing
Without marketing, We may need a pair of binoculars to find our app.
2. Prepare app for release
Finalize code, design and marketing for the app release. We make sure to test your app thoroughly!
3. Cross your finger
Untill the app does not satisfy our customer, we monitor the crash report and user feedback
carefully.
4. App Maintenance
A good app developer releases updates that fix bugs and crashes, that what we do.